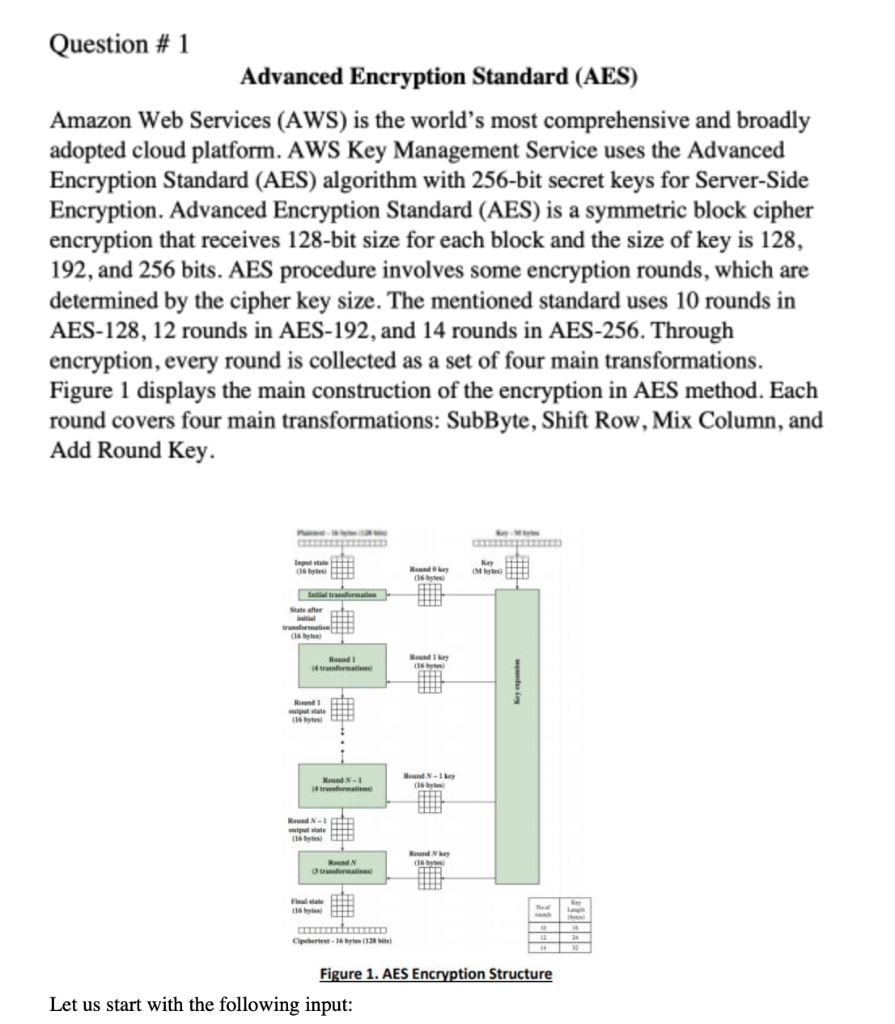
![PDF] Investigating the Effects of varying the Key Size on the Performance of AES Algorithm for Encryption of Data over a Communication Channel | Semantic Scholar PDF] Investigating the Effects of varying the Key Size on the Performance of AES Algorithm for Encryption of Data over a Communication Channel | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/da6c8b9a0aba014f56454994af710a708f61dc5e/3-Table1-1.png)
PDF] Investigating the Effects of varying the Key Size on the Performance of AES Algorithm for Encryption of Data over a Communication Channel | Semantic Scholar

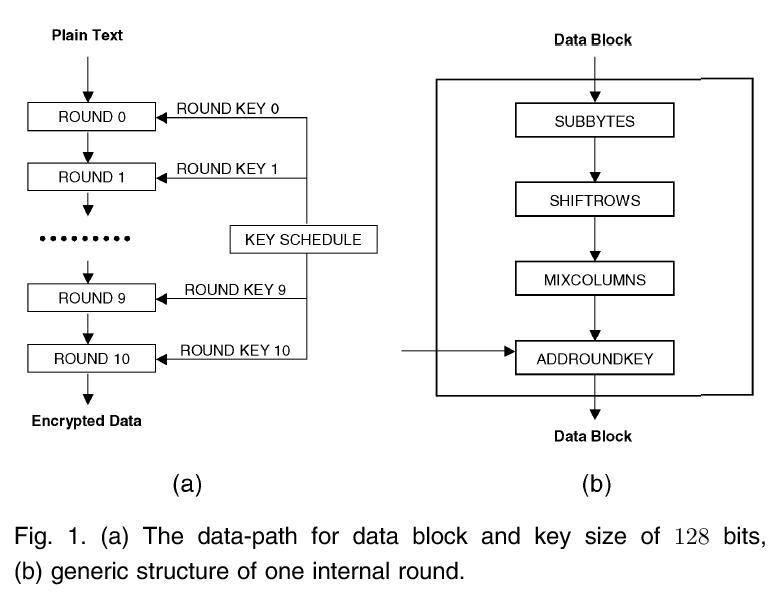
Figure 2 from Investigating the Effects of varying the Key Size on the Performance of AES Algorithm for Encryption of Data over a Communication Channel | Semantic Scholar

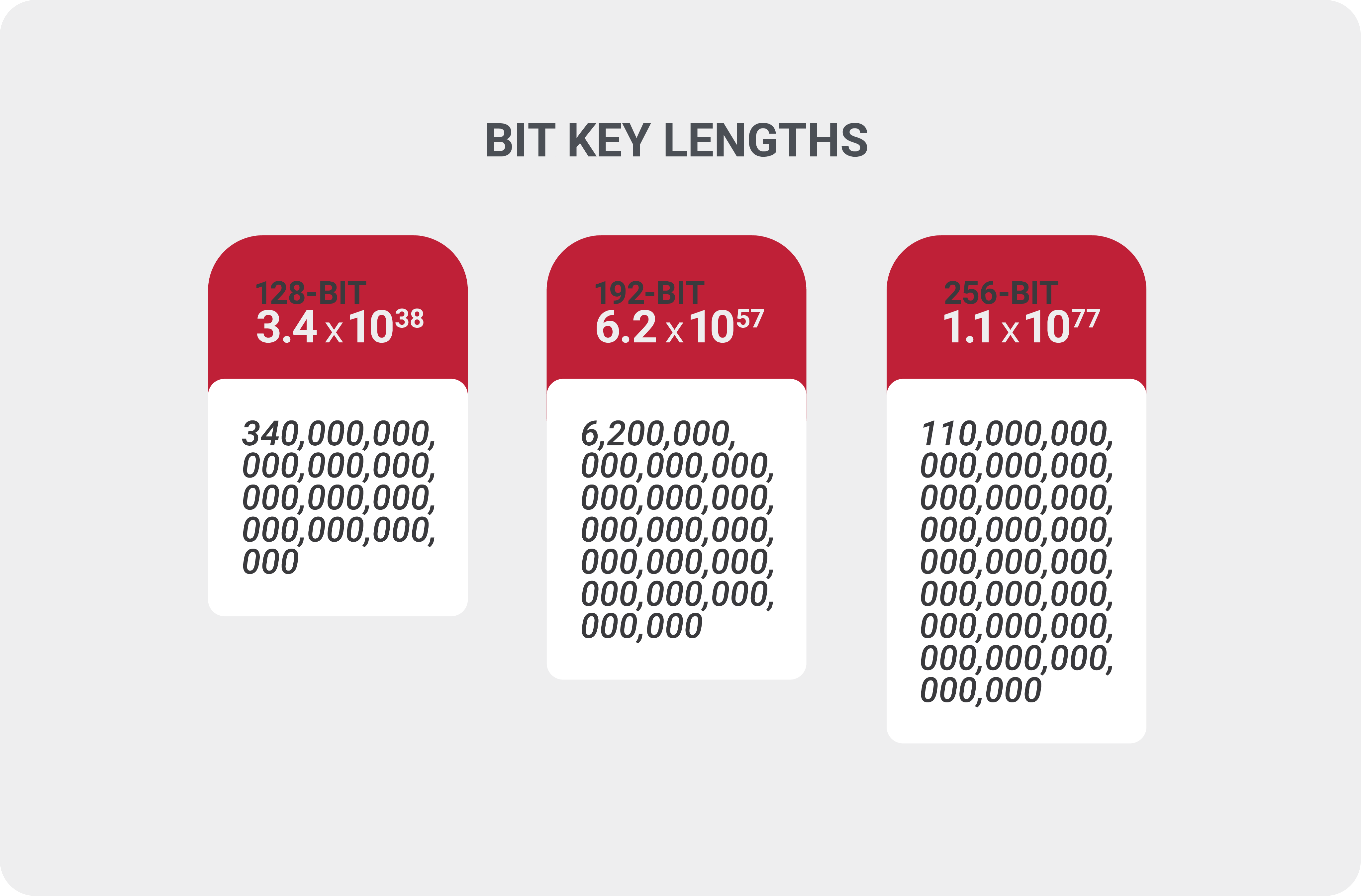
Comparison Of Blowfish, Aes, Triple Des And Des Algorithms For Block... | Download Scientific Diagram
![PDF] Investigating the Effects of varying the Key Size on the Performance of AES Algorithm for Encryption of Data over a Communication Channel | Semantic Scholar PDF] Investigating the Effects of varying the Key Size on the Performance of AES Algorithm for Encryption of Data over a Communication Channel | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/da6c8b9a0aba014f56454994af710a708f61dc5e/3-Table2-1.png)



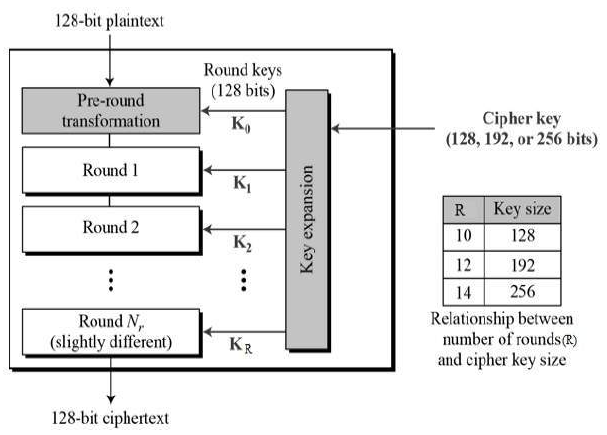
![PDF] AES Algorithm Using 512 Bit Key Implementationfor Secure Communication | Semantic Scholar PDF] AES Algorithm Using 512 Bit Key Implementationfor Secure Communication | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/e8ff102e130ccdfa1054059a4da33d9cd1089fd0/6-Figure4-1.png)