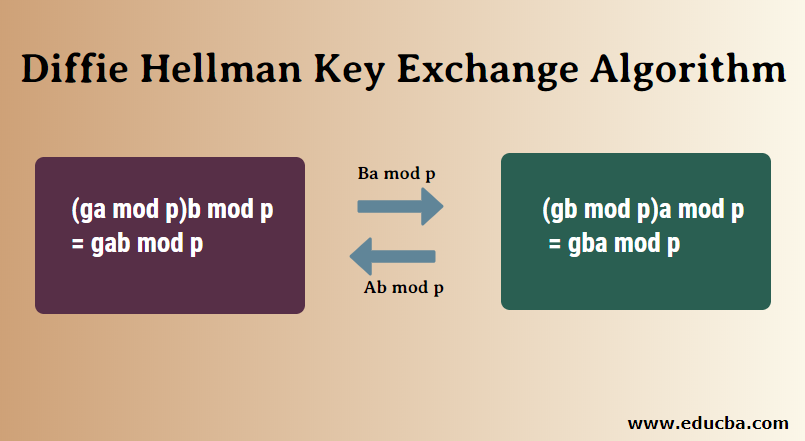
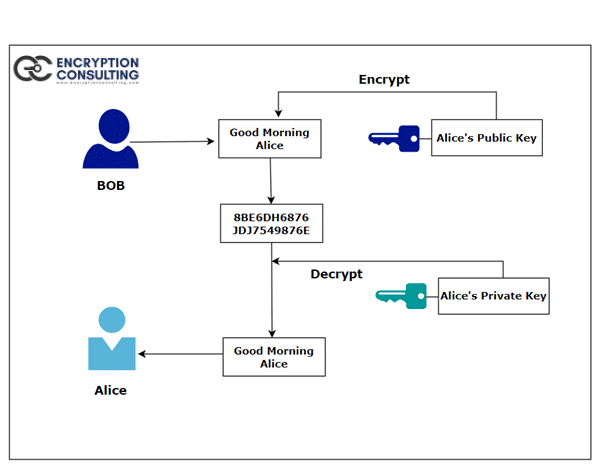
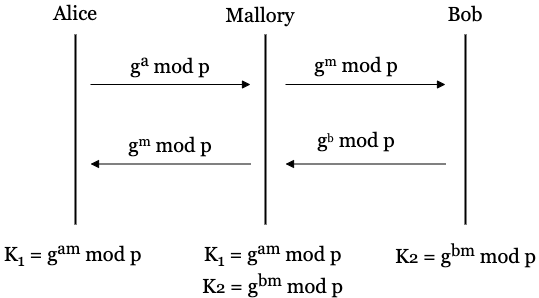
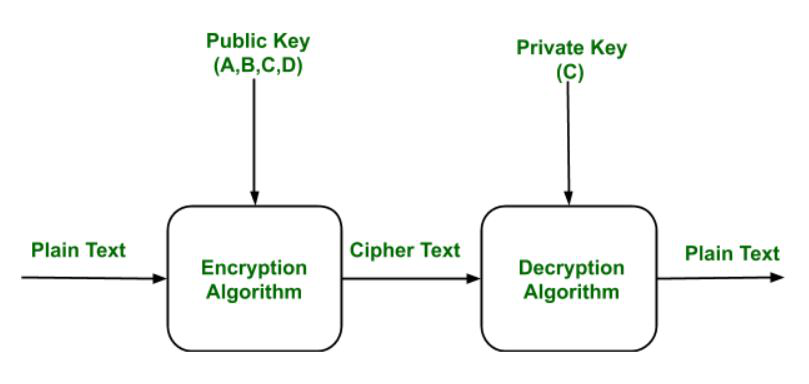
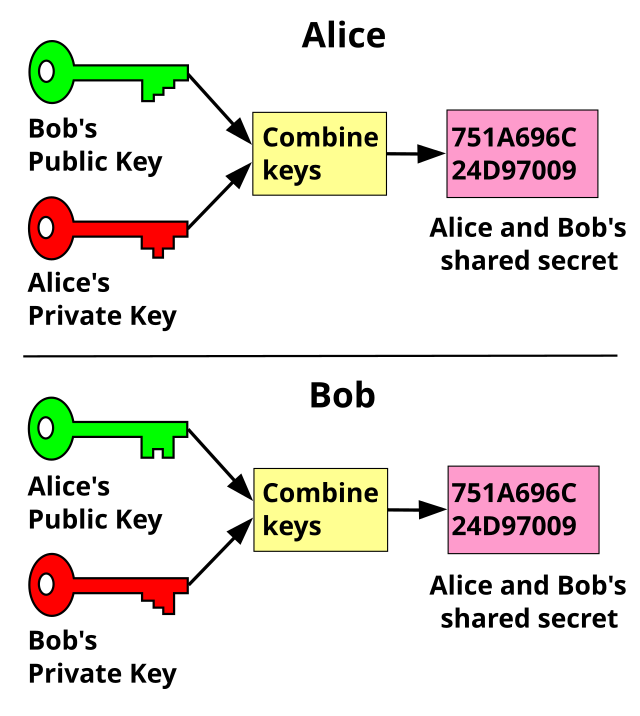
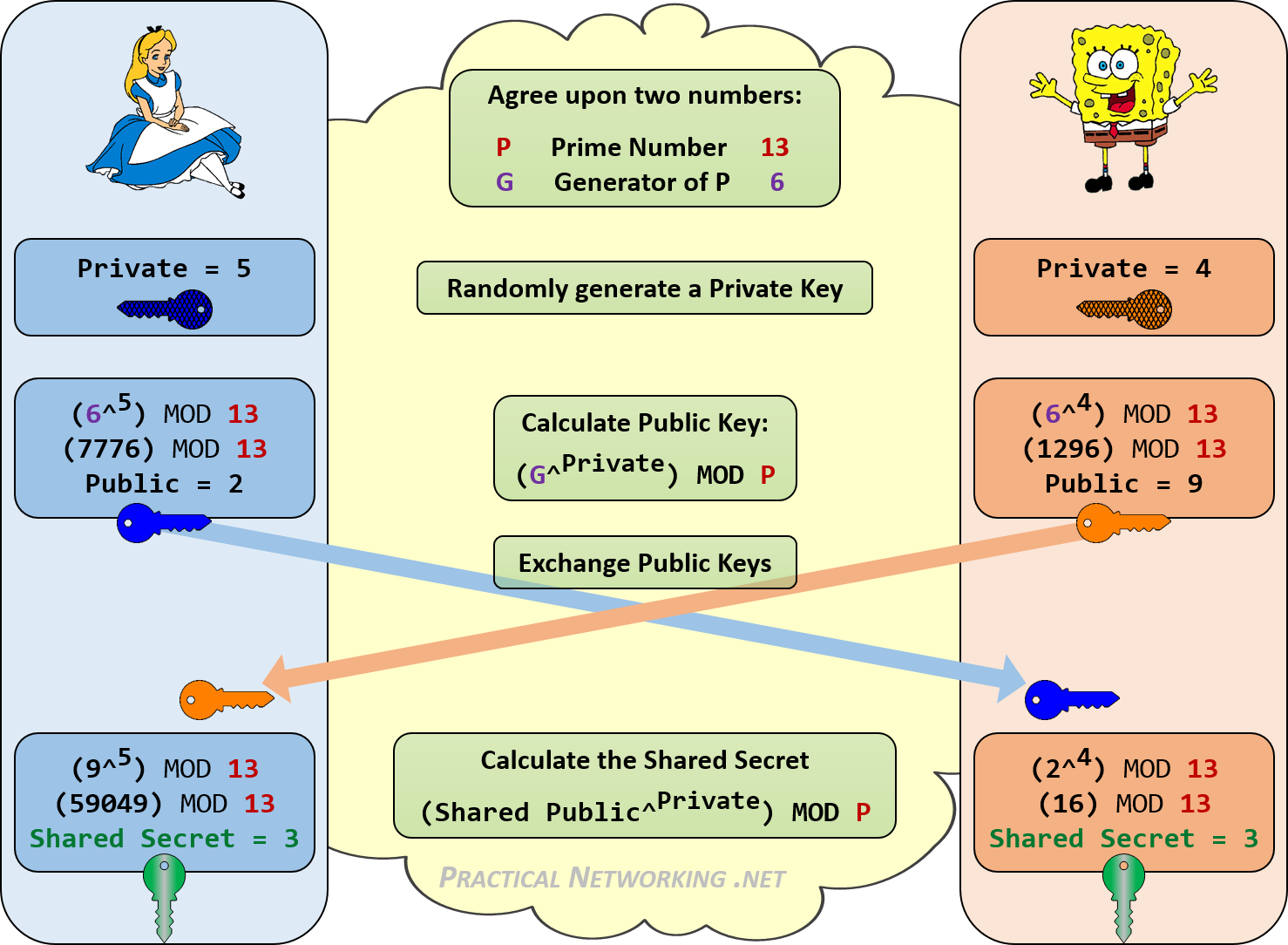
Diffie-Hellman Key Exchange - the MAGIC that makes it possible - Cryptography - Practical TLS - YouTube
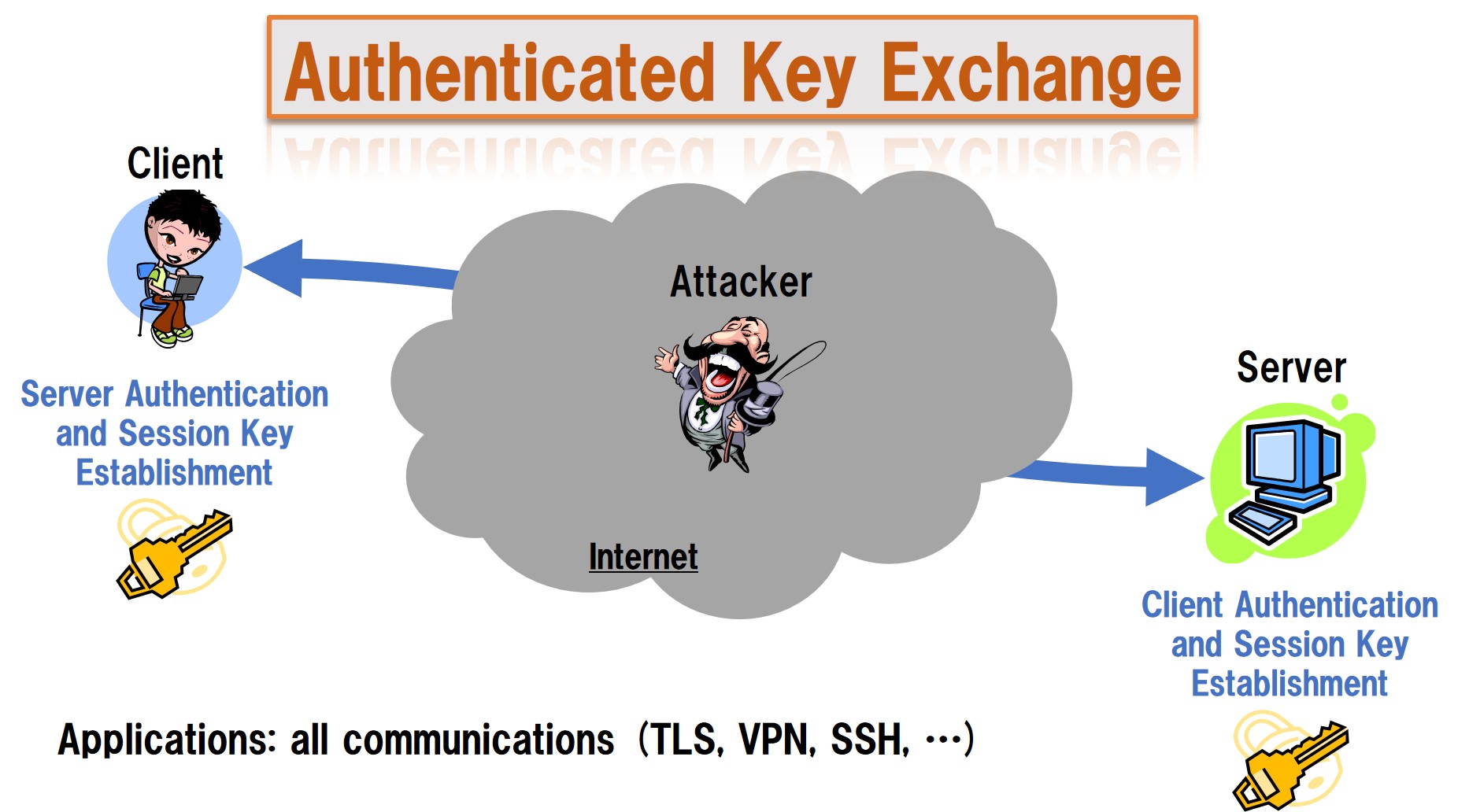
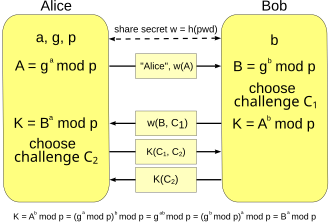
Cryptographic Authentication and Key Exchange - Security Assurance Scheme Research Team | Cyber Physical Security Research Center - AIST