گرگــ گرافیکــــ - دانلود برنامه هک یو اس بی usb stealer http://wolfgraphic.us/264/%D8%AF%D8%A7%D9%86%D9%84%D9%88%D8%AF-%D8%A8%D8%B1%D9%86%D8%A7%D9%85%D9%87- usb-stealer/ | Facebook

USB Stealer, Just like those unrealistic movies and TV shows, except this one's real. - Leewardslope

Sandisk 32 GB USB Flash Drive - SDIX30N-032G-GNAOA : Buy Online at Best Price in KSA - Souq is now Amazon.sa: Electronics
GitHub - stevdza-san/USB-Stealer-Linux-OS: Well this USB stealer is not the same as in Windows OS, because on Linux you don't have permission to run scripts direct from USB. That's why you would
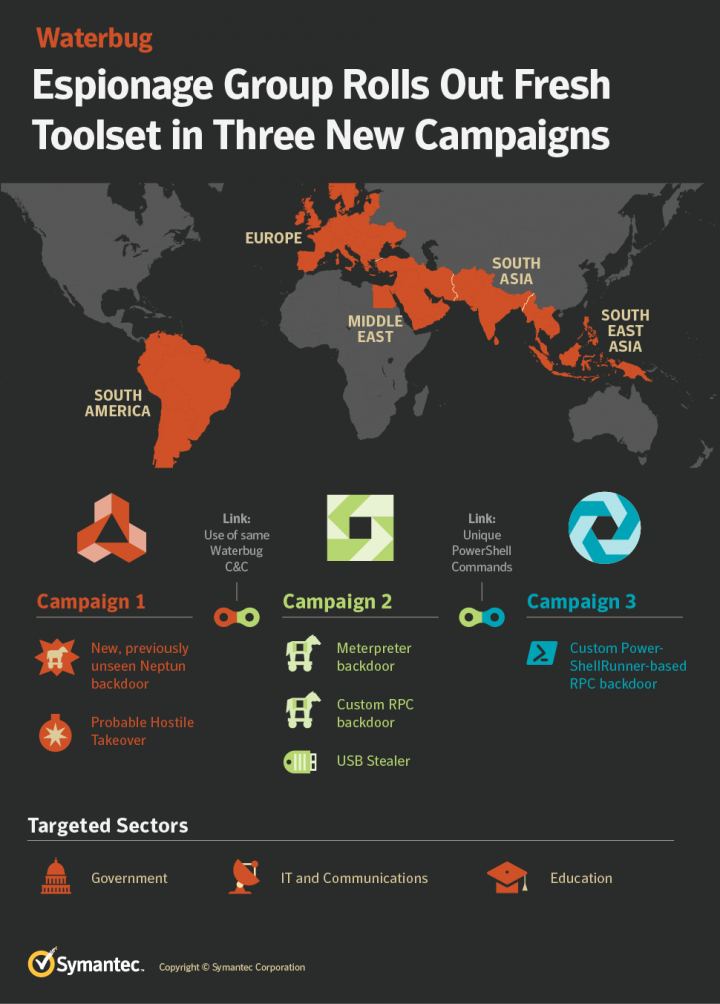
Waterbug: Espionage Group Rolls Out Brand-New Toolset in Attacks Against Governments | Symantec Enterprise Blogs









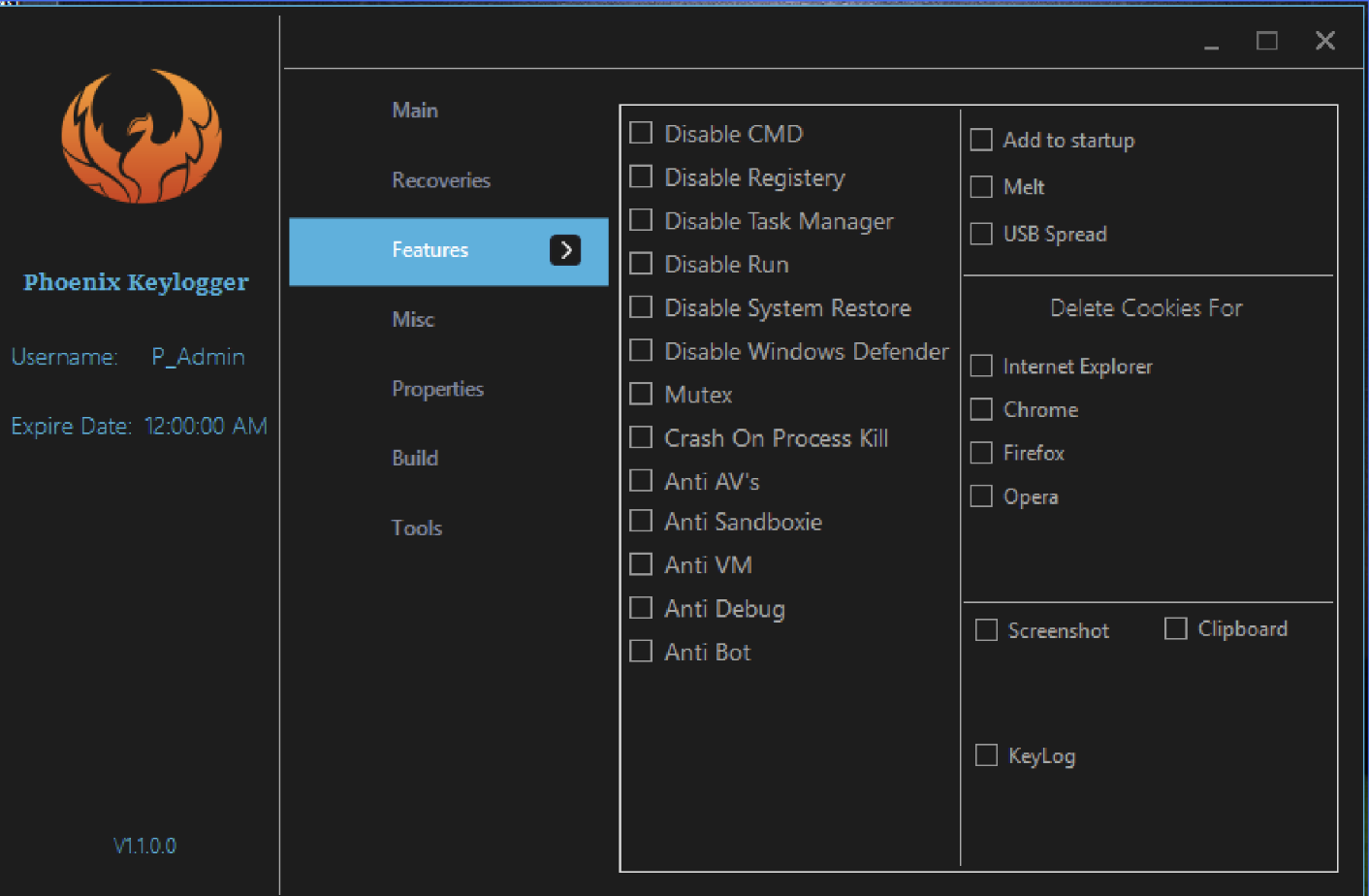
/cdn.vox-cdn.com/uploads/chorus_asset/file/23949203/226141_rubberDucky.jpg)